D-Link COVR-1102 Password Truncation Vulnerability
I discovered a vulnerability in the D-Link COVR-1102 AC1200 Dual Band Whole Home Mesh Wi-Fi System (Hardware Version: B1, Firmware Version <= 2.02). Affected devices were discovered to truncate Wi-Fi Protected Access Pre-Shared Keys (WPA-PSK) for a wireless network SSID, if the WPA-PSK set by a user on the primary Wi-Fi node / access point contains whitespace. Under these conditions, it is possible to authenticate to a secondary Wi-Fi node / access point connected to the network using a substring of the WPA-PSK. This could allow an attacker to discover a much weaker WPA-PSK and obtain access to the network connected to the Wi-Fi router via a brute-force attack on the WPA-PSK.
Details
Product: D-Link COVR-1100, 1102, 1103 AC1200 Dual Band Whole Home Mesh Wi-Fi System
Affected Versions: Tested on Hardware Version B1, Firmware Version 2.02. Only tested on COVR-1100_fw_revb_202b01_ALL_multi_20221230, other versions may be affected too
Fixed Versions: Not fixed at the time of publication
Vulnerability Type: Input validation, weak authentication
Security Risk: Medium
Advisory URL: https://exploots.github.io/posts/2024/01/18/d-link-covr-1102-vulnerability.html
Advisory Status: Published
CVE: CVE-2023-52043
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-52043
Introduction
The D-Link COVR-1102 is Dual-Band Whole Home Mesh Wi-Fi System (Wi-Fi Router).
Technical Details
During set up of the D-Link COVR Mesh Wi-Fi system in a home environment, I was experiencing difficulties connecting roaming client devices to a secondary node within the Wi-Fi mesh system. After some troubleshooting efforts, the cause of the roaming / connectivity issues was found to be that the secondary node was not able to be authenticated to with the password saved on multiple wireless clients. At this time, the WPA-PSK used was a passphrase, containing whitespace (space character).
Suspecting initially that faulty hardware was thought to be causing issues, a support ticket was raised with the vendor. The vendor support team was able to resolve the issue and responded with advice to not use whitespace in the WPA-PSK, which is typical of passphrases. Modifying the password (without whitespace) did solve the connectivity issues. However, this made me curious about the cause of the initial issues, and prompted further investigations into potential security impacts from a network security perspective.
From the observations, whitespace may be improperly handled by the device firmware. Through further manual testing on the home wireless network, it was discovered that the WPA-PSK was actually being truncated after the first whitespace character on the secondary wireless access points within the COVR mesh Wi-Fi system. Supplying a truncated password allowed for a client device to authenticate to the network.
It was concluded that the vulnerability occurs when synchronising network service data between primary and secondary wireless access points. When a user sets a WPA-PSK containing whitespace, the WPA- PSK string is truncated after the first whitespace character prior to this synchronisation across the wireless mesh network, creating a substring leading to resultant authentication weaknesses in the secondary access points.
The vulnerability can be exploited by brute force attacks, or password guessing. Attacks on WPA / WPA2 networks and PSKs can be performed using known attack techniques.
Proof of Concept
Steps to reproduce the security vulnerability are detailed below.
- The D-Link Device Administration Console allows for setting a WPA-PSK containing whitespace characters, due to a lack of input validation, shown in Figure 1.
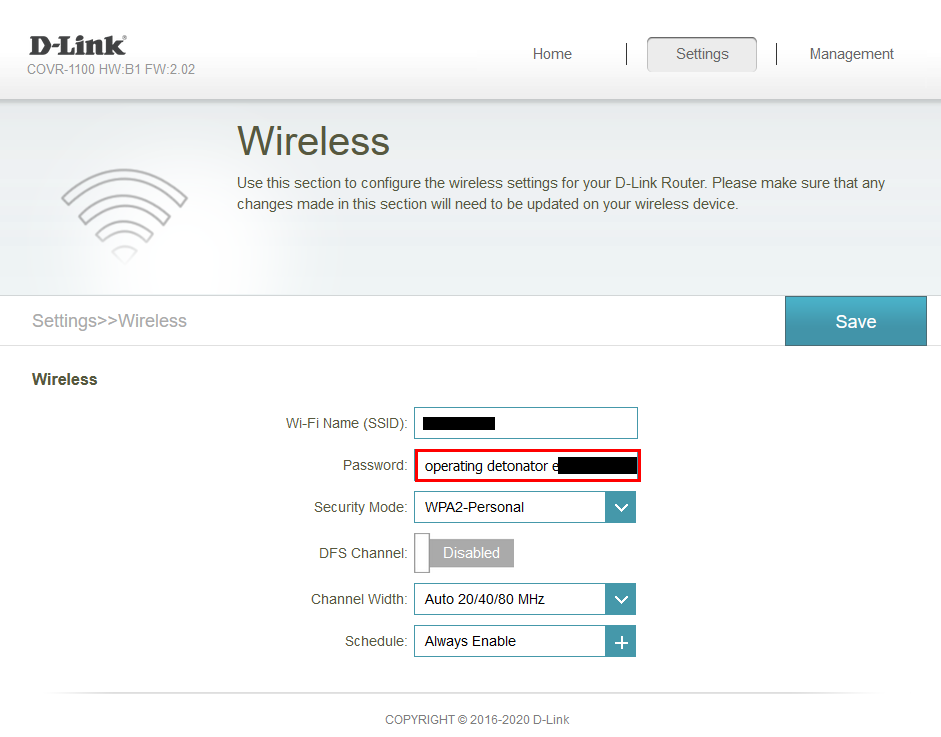
Figure 1: Setting a WPA-PSK containing whitespace
- Connect to the primary access point / “main node” within the Wi-Fi mesh network using the entire password string. The provided screenshot in Figure 2 shows the full password required to authenticate with the wireless access point, which is the expected behaviour. The wireless client device will now be connected to the wireless network.
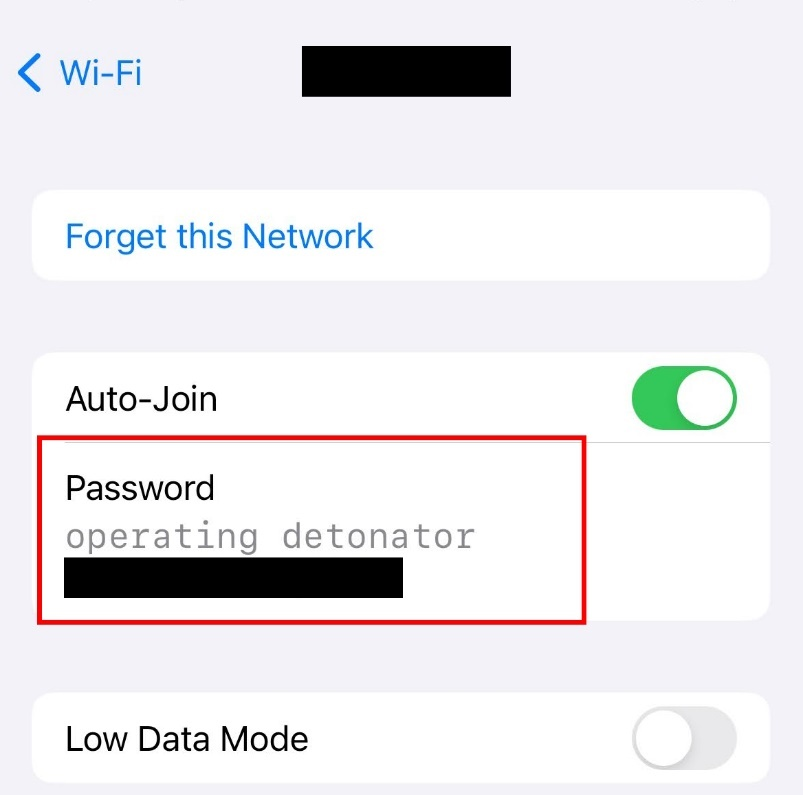
Figure 2: Connecting the wireless client device to the primary wireless access point with full WPA-PSK string
- Force Wi-Fi roaming to occur in the mesh system by moving the connected wireless client device outside of the usable range of the primary access point and within close proximity to connect to the secondary access point. Figure 3 shows the wireless client device is now unable to authenticate to the wireless local network, creating a localised Denial of Service condition within the Customer’s LAN.
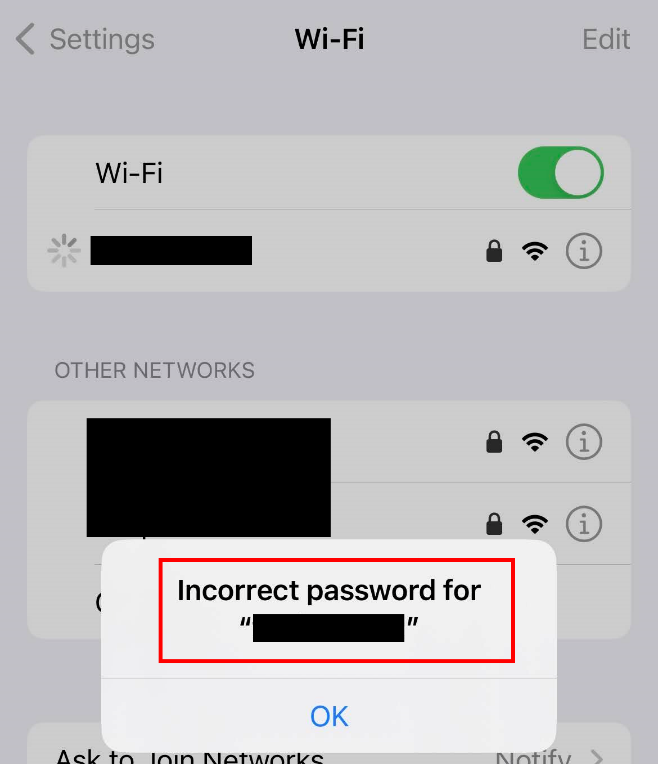
Figure 3: Denial of Service to local network due to authentication error
- Figure 4 shows that the truncated password substring is used by wireless client device. The wireless client device is now connected to the secondary access point.
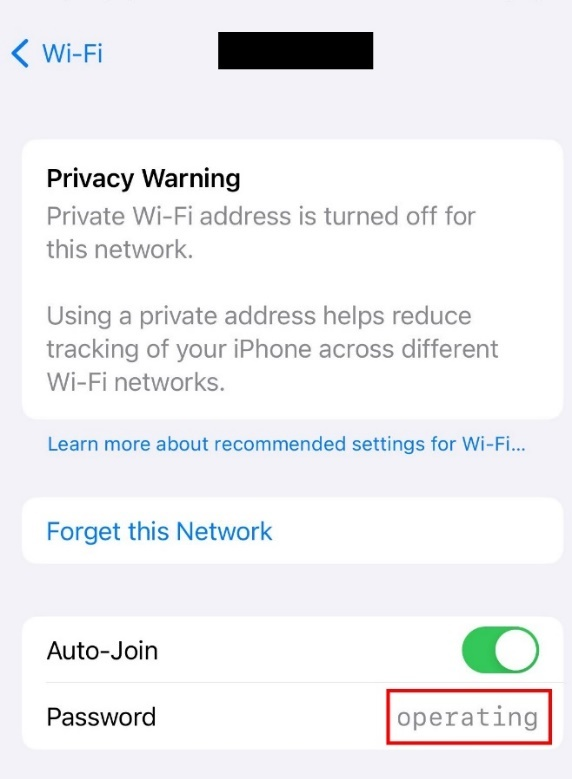
Figure 4: Connecting the wireless client device to the secondary access point using the truncated WPA-PSK substring
Security Risk
Attackers that are physically located in the Wi-Fi range of the mesh network may leverage this vulnerability to obtain access to the local network connected to the Wi-Fi router.
A loss of integrity is limited to the WPA-PSK (the password) itself, and a loss of availability affects parts of the wireless mesh network.
More severe impacts (e.g., network compromise) may result from chaining vulnerabilities together, say if the weaker password can be brute-forced.
The following impacts apply to Customers / Consumers using the Wi-Fi router on their networks:
- Malicious parties might succeed in authentication by providing a smaller password (substring) that matches the associated portion of the larger, correct password if attacks are targeted to secondary access points. This significantly reduces the key search space for an attacker, making brute force or password guessing attacks on the wireless network more feasible.
- Denial of Service to the customer’s local area network (LAN) when in proximity of the secondary access point, when using ‘saved passwords’ on roaming devices due to the mismatched password strings.
As a result, this vulnerability is rated to pose a medium risk.
References
Disclosure Timeline
15-Sept-2023 - Initial bug identified
21-Sept-2023 - Further research and classify bug as a security vulnerability
21-Sept-2023 - Issue submitted to D-Link Security Team (via email: security@dlink.com)
11-Oct-2023 - Acknowledgement of report by D-Link Security Team
23-Dec-2023 - CVE ID requested
18-Jan-2024 - CVE-2023-52043 reserved by MITRE
18-Jan-2024 - Advisory released (this blog post)
24-Mar-2024 - No further action by D-Link (6 months since initial notification), send update to MITRE regarding reserved status